Authenticate with ArcGIS Online (or your own portal) using OAuth2 to access secured resources (such as private web maps or layers). Accessing secured items requires logging in to the portal that hosts them (an ArcGIS Online account, for example).
Use case
Your app may need to access items that are only shared with authorized users. For example, your organization may host private data layers or feature services that are only accessible to verified users. You may also need to take advantage of premium ArcGIS Online services, such as geocoding or routing services, which require a named user login.
How to use the sample
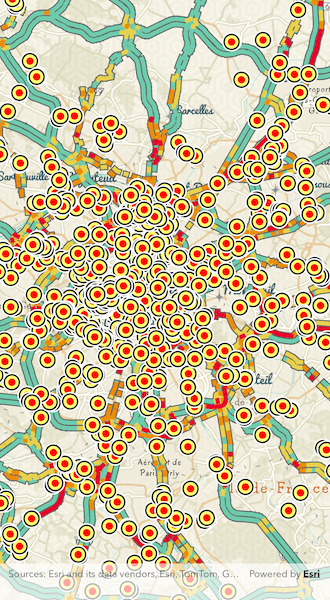
When you run the sample, the app will load a web map which contains premium content. You will be challenged for an ArcGIS Online login to view the private layers. Enter a user name and password for an ArcGIS Online named user account (such as your ArcGIS Location Platform account). If you authenticate successfully, the traffic layer will display, otherwise the map will contain only the public basemap layer.
How it works
- Create an
OAuthConfigurationspecifying the portal URL, client ID, and redirect URL. - Create a toolkit component
Authenticatorwidget with the OAuth user configuration. - Load a map with premium content from a
PortalItemrequiring authentication to automatically invoke the authentication challenge.
Relevant API
- Authenticator
- OAuthConfiguration
- Portal
- PortalItem
Additional information
The workflow presented in this sample works for all SAML based enterprise (IWA, PKI, Okta, etc.) & social (facebook, google, etc.) identity providers for ArcGIS Online or Portal. For more information, see the topic Set up enterprise logins.
For additional information on using Oauth in your app, see the topic Authorization code flow with PKCE.
Tags
authentication, cloud, credential, OAuth, portal, security
Sample Code
//
// Copyright 2024 Esri
//
// Licensed under the Apache License, Version 2.0 (the "License");
// you may not use this file except in compliance with the License.
// You may obtain a copy of the License at
//
// https://www.apache.org/licenses/LICENSE-2.0
//
// Unless required by applicable law or agreed to in writing, software
// distributed under the License is distributed on an "AS IS" BASIS,
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
// See the License for the specific language governing permissions and
// limitations under the License.
//
import 'package:arcgis_maps/arcgis_maps.dart';
import 'package:arcgis_maps_sdk_flutter_samples/common/common.dart';
import 'package:arcgis_maps_toolkit/arcgis_maps_toolkit.dart';
import 'package:flutter/material.dart';
class AuthenticateWithOAuth extends StatefulWidget {
const AuthenticateWithOAuth({super.key});
@override
State<AuthenticateWithOAuth> createState() => _AuthenticateWithOAuthState();
}
class _AuthenticateWithOAuthState extends State<AuthenticateWithOAuth>
with SampleStateSupport {
// Create a controller for the map view.
final _mapViewController = ArcGISMapView.createController();
// Create an OAuthUserConfiguration.
// This document describes the steps to configure OAuth for your app:
// https://developers.arcgis.com/documentation/security-and-authentication/user-authentication/flows/authorization-code-with-pkce/
final _oauthUserConfiguration = OAuthUserConfiguration(
portalUri: Uri.parse('https://www.arcgis.com'),
clientId: 'T0A3SudETrIQndd2',
redirectUri: Uri.parse('my-ags-flutter-app://auth'),
);
@override
void dispose() {
// Revoke OAuth tokens and remove all credentials to log out.
Authenticator.revokeOAuthTokens()
.catchError((error) {
// This sample has been disposed, so we can only report errors to the console.
// ignore: avoid_print
print('Error revoking tokens: $error');
})
.whenComplete(Authenticator.clearCredentials);
super.dispose();
}
@override
Widget build(BuildContext context) {
return Scaffold(
// Add an Authenticator to handle authentication challenges.
body: Authenticator(
// Provide the OAuthUserConfiguration to the Authenticator.
oAuthUserConfigurations: [_oauthUserConfiguration],
// Add a map view to the widget tree and set a controller.
child: ArcGISMapView(
controllerProvider: () => _mapViewController,
onMapViewReady: onMapViewReady,
),
),
);
}
void onMapViewReady() {
// Create a map from a web map that has a secure layer (traffic).
final portalItem = PortalItem.withPortalAndItemId(
portal: Portal.arcGISOnline(connection: PortalConnection.authenticated),
itemId: 'e5039444ef3c48b8a8fdc9227f9be7c1',
);
final map = ArcGISMap.withItem(portalItem);
// Set the map to map view controller.
_mapViewController.arcGISMap = map;
}
}