ArcGIS supports secure access to ArcGIS services and portal items. It ensures that only valid, authorized users and services can access protected information. To access secure ArcGIS resources, you need an access token that you can obtain by implementing an authentication workflow in your app. The type of authentication you use will depend on the security and access requirements of your app.
There are three types of authentication that you can use to get an access token:
- API key authentication: grants a long-lived access token to authenticate requests to ArcGIS services and secure portal items. For more information see the Introduction to API key authentication. To obtain an API key access token, go to the Create an API key tutorial using your ArcGIS account. Here you can configure the API key privileges to authorize access to different services and portal items.
- API key access tokens created with an ArcGIS Enterprise account, from ArcGIS Enterprise in version 11.4 onwards, provide access to secure items in an ArcGIS Enterprise portal.
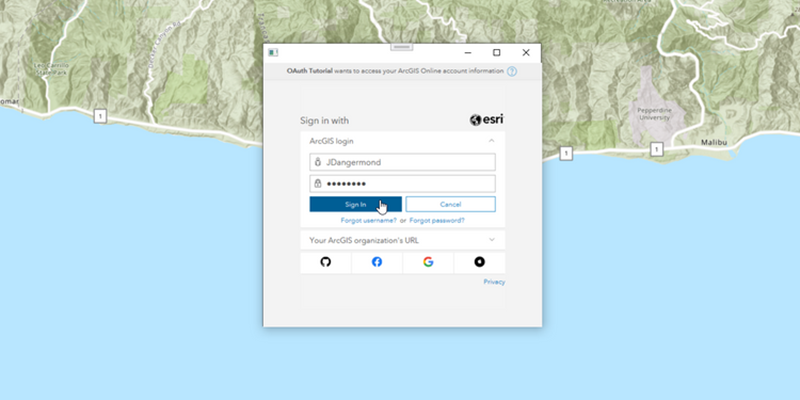
- User authentication: grants a short-lived token, generated via OAuth, giving your application permission to access the ArcGIS services and secure portal items authorized to an existing ArcGIS user's account.
- App authentication: grants a short-lived access token via OAuth 2.0, authorizing your application to access ArcGIS services and secure portal items.
To make authenticated requests to services, you need to set the token parameter to an access token.
For more information, see the Security and authentication guide.
Choose a type of authentication
The following considerations can help determine which type of authentication to implement:
-
Access to resources—Your app can access ArcGIS services and portal items using API key authentication, User authentication, or App authentication.
-
User experience—If you don't want to make users log in, your app can access ArcGIS services using API key authentication or App authentication. In this case, users will not need to have an ArcGIS account in order to use your app.
-
Usage charges—If you want service usage to be charged to the user's account, your app must request that the user log in using User authentication. When using API key authentication or App authentication, all access to services from your app will be charged to your ArcGIS account.
You might also need to consider the level of security required for your app, how your app will be distributed, and your available ArcGIS products and accounts.
| Scenario | Solution |
|---|---|
| Your app requires access to ArcGIS services only, you don't want to make users log in, and you are willing to pay for all charges incurred from usage of the app. | API key authentication or App authentication |
| Your app requires access to location services only and you want usage charged to the user. | User authentication |
| Your app needs to access content that requires an ArcGIS Online subscription. | User authentication |
| Your app needs to access private hosted data on your ArcGIS Location Platform account. | API key authentication or App authentication |
| Your app allows users to view and edit private data hosted in ArcGIS Online or ArcGIS Enterprise. | User authentication |
| You plan to distribute your app through ArcGIS Marketplace. | User authentication |
API key authentication
An API key can grant your public-facing application access to specific ArcGIS services and portal items.
Use API key authentication when you want to:
- Quickly write applications that consume ArcGIS services.
- Provide access to services without requiring users to sign in with an ArcGIS account.
Use API key access tokens
An API key, can be used to authorize access to specific ArcGIS services and portal items. Go to the Create an API key tutorial to obtain a new access token.
If you set the access token on the ArcGISRuntimeEnvironment, all requests made by your app will be authorized using this token. You will be able to view the app's usage telemetry on the respective ArcGIS Location Platform, ArcGIS Online, or ArcGIS Enterprise account.
You can also set the access token on any class that implements ApiKeyResource. When you set an access token for a specific class, it will override any access token you may have set on ArcGISRuntimeEnvironment, enabling more granular usage telemetry and management for ArcGIS Online resources used by your app.
Classes that implement ApiKeyResource include:
-
ArcGISSceneLayer -
ArcGISTiledLayer -
ArcGISVectorTiledLayer -
Basemap -
ClosestFacilityTask -
ExportTileCacheTask -
ExportVectorTilesTask -
GeodatabaseSyncTask -
LocatorTask -
RouteTask -
ServiceAreaTask -
ServiceFeatureTable
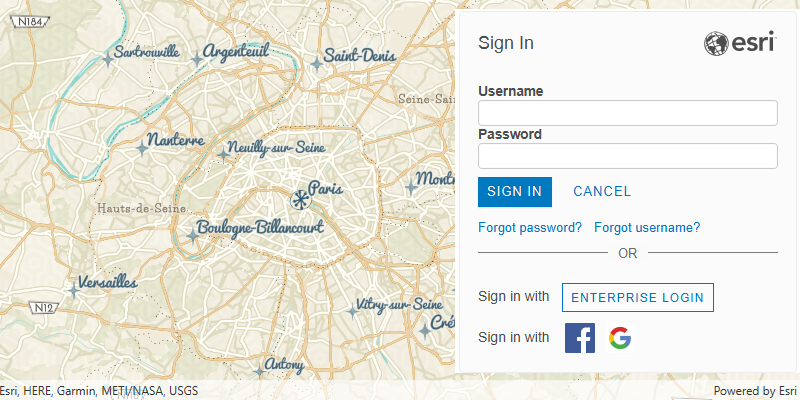
User authentication
User authentication is a set of authentication workflows that allow users with an ArcGIS account to sign into an application and access ArcGIS content, services, and resources. The typical authentication protocol used is OAuth2.0. When a user signs into an application with their ArcGIS account, an access token is generated that authorizes the application to access services and content on their behalf. The resources and functionality available depend on the user type, roles, and privileges of the user's ArcGIS account.
Services that your app accesses with user authentication will be billed to the authenticated user's ArcGIS account and its associated ArcGIS subscription. If your application will access your users' secure content in ArcGIS or if you plan to distribute your application through ArcGIS Marketplace, you must use user authentication.
Implement user authentication when you want to:
- Ensure users are signed in and authenticated with their own ArcGIS account.
- Use your app user's credits to pay for their private data, content, or service transactions.
- Limit the length of time users can be signed in to your app with a temporary token.
- Distribute your app through ArcGIS Marketplace.
App authentication
App authentication grants a short-lived access token, generated via OAuth 2.0, authorizing your application to access ArcGIS location services, such as basemap layers, search, and routing.
Use app authentication when you want to:
- Access location services with a more secure process and a short-lived token.
- Provide access to services without requiring users to have an ArcGIS account.
Authentication manager
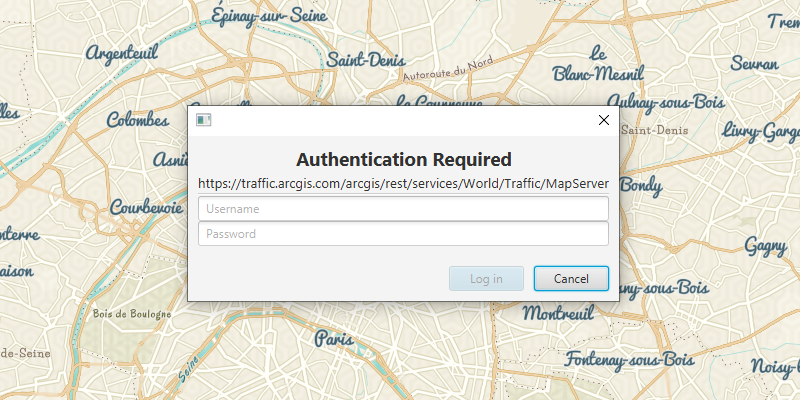
This API contains an AuthenticationManager, available from the ArcGISRuntimeEnvironment, that manages all user authentication when your application connects to secured resources. It provides a central place to configure the authentication challenge handlers and credential stores.
AuthenticationManager manages user authentication when connecting to secured services and provides a central place to configure the following aspects of authentication:
Set a central authentication challenge handler that will allow your users to authenticate with secured services
The DefaultAuthenticationChallengeHandler class can take care of user credential and OAuth challenges. For other challenges you must implement AuthenticationChallengeHandler and pass an instance of your handler to set.
The AuthenticationManager's AuthenticationChallengeHandler is null by default; if no handler is set, the request to the secured resource will fail as it cannot be authenticated; for example, a Loadable that uses a secured resource may have a Load and the Loadable.get will indicate an authorization failure.
Manage an in-memory cache of credentials
When a user is challenged and enters credentials which successfully allow access to the resource, those credentials are automatically added to the AuthenticationManager.CredentialCache. When secured resources from the same server and port are accessed subsequently, credentials in this cache are reused automatically, avoiding unnecessary challenges. Certificates are also cached, see below for more details.
If your app allows a user to sign out of a portal or server, call Authentication to remove all cached credentials when the user signs out, to prevent users accessing resources for which they do not have permission.
The credential cache can be serialized to json, enabling it to be stored between app sessions. However, the serialized credential cache should be secured using an appropriate mechanism for your platform to ensure that credentials are not available to other apps or processes.
Manage the certificates for accessing certificate secured resources
Authentication challenges issued for self-signed server certificates can be handled as follows. Use the set method to provide a listener that will handle self signed certificates as they are encountered (Other types of AuthenticationChallenge will continue to be sent to the current AuthenticationChallengeHandler). This approach is useful when you want to add specific logic for trusting self-signed certificates on a case-by-case basis, but the behavior of the DefaultAuthenticationChallengeHandler is suitable for all other authentication challenges.
For testing purposes, set can be called with a value of true to indicate an app is willing to trust all valid, non-expired, self-signed certificates. This should never be used in production code.
Manage a set of OAuth configurations
If your app will connect to OAuth secured resources, and you have set an instance of the DefaultAuthenticationChallengeHandler onto the AuthenticationManager, then add an OAuthConfiguration for a specific Client ID and portal by calling add. The set of OAuthConfiguration is stored in-memory only and does not persist between sessions.
What's Next?
For more information about Security and Authentication, see the Security and Authentication chapter.